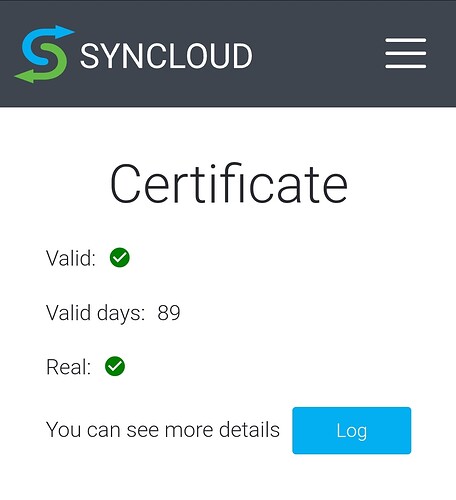
good! Web interface works. Now I have activated my device with a new name. I don’t think it will work for certification but it’s yet to be tested. I’ll let you know how it works
the situation is the following: for reasons that I ignore, Chrome now allows me to access to the web interface without certificate (no https), see picture below, before the last changes it was not possible. I don’t thin it is satisfactory but that is:
here follows what I see in the page “access”. Is the switch “public” useful to disable external access?
thx
SB
] without certificate (no https)
Usually browsers allow you to access https websites with wrong certificate after you accept the risk warning
Is the switch “public” useful to disable external access?
Yes this switch instructs the device to create a dns record based on piblic ip v4.
I have pushed one more change, could you update system and later send logs please?
Hi,
in this version of the platform, logs are printed directly in the web page:
so, I make a copy&paste in mail msg to support. Ciao
SB
I was always loke this, please for support still use Settings - Support as it has more info and easier to analyse.
I’d like to, but the button has disappeared ![]()
update: support page is back with the original layout. Just sent you logs
Can you try running this command to see if you get responses with answer section in them, bare in mind this record is created for 10 minutes and then removed for 5 minutes, so the test is to see that as soon as it starts to appear it appears constantly for few minutes.
curl -i 'https://dns.google/resolve?name=_acme-challenge.simobu.syncloud.it&type=txt&do=1'
Good response looks like this:
`HTTP/2 200
x-content-type-options: nosniff
strict-transport-security: max-age=31536000; includeSubDomains; preload
access-control-allow-origin: *
date: Sun, 08 Dec 2024 12:48:30 GMT
expires: Sun, 08 Dec 2024 12:48:30 GMT
cache-control: private, max-age=10
content-type: application/json; charset=UTF-8
server: HTTP server (unknown)
x-xss-protection: 0
x-frame-options: SAMEORIGIN
alt-svc: h3=“:443”; ma=2592000,h3-29=“:443”; ma=2592000
accept-ranges: none
vary: Accept-Encoding
{“Status”:0,“TC”:false,“RD”:true,“RA”:true,“AD”:false,“CD”:false,“Question”:[{“name”:“_acme-challenge.simobu.syncloud.it.”,“type”:16}],“Answer”:[{“name”:“_acme-challenge.simobu.syncloud.it.”,“type”:16,“TTL”:10,“data”:“STU8-LnB6s17G5HOWe0xznZQE8iqBTUNmcyCpxssk5I”},{“name”:“_acme-challenge.simobu.syncloud.it.”,“type”:16,“TTL”:10,“data”:“pRqd-T3Gk_XZp8kVmEvUa2H285ymvzDvbtnjGSybZGk”}],“Comment”:“Response from 205.251.199.8.”}`
I have run it just once, it looks good, doesn’t it?
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Dec 7 16:37:07 2024 from 192.168.1.12
root@syncloud:~# curl -i 'https://dns.google/resolve?name=_acme-challenge.simobu.syncloud.it&type=txt&do=1'
HTTP/2 200
x-content-type-options: nosniff
strict-transport-security: max-age=31536000; includeSubDomains; preload
access-control-allow-origin: *
date: Sun, 08 Dec 2024 15:19:12 GMT
expires: Sun, 08 Dec 2024 15:19:12 GMT
cache-control: private, max-age=10
content-type: application/json; charset=UTF-8
server: HTTP server (unknown)
x-xss-protection: 0
x-frame-options: SAMEORIGIN
alt-svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
accept-ranges: none
vary: Accept-Encoding
{"Status":0,"TC":false,"RD":true,"RA":true,"AD":false,"CD":false,"Question":[{"name":"_acme-challenge.simobu.syncloud.it.","type":16}],"Answer":[{"name":"_acme-challenge.simobu.syncloud.it.","type":16,"TTL":10,"data":"KoWW-patfuKvoUZcPY18gp6MuJZk1kmkdVcM5ph5nsg"},{"name":"_acme-challenge.simobu.syncloud.it.","type":16,"TTL":10,"data":"82tUd3YbQsu9Ek6Q-etdZxZYepe5WI73RSsqW24CrTw"}],"Comment":"Response from 205.251.193.183."}root@syncloud:~#
Yes.
Ok one more fix could you upgrade system and send logs please?
Great, I managed disable the checks which were still using the locally provided dns.
I think your provider is providing bad dns servers (not very unusual) but it does not really filter direct calls to external dns (have not seen so far).
Hopefully it will stay like this for some time, let me know if somethig goes wrong again ![]()